 In the first blog of this series we looked at what the features of Microsoft Intune App-Layer protection are, in the second blog we wrapped a custom application with the Microsoft Intune Application Wrapper. So now that we have a custom application and an application enabled for management via Microsoft Intune that we are able to deploy them via Microsoft Intune and see the different behavior of the same application.
In the first blog of this series we looked at what the features of Microsoft Intune App-Layer protection are, in the second blog we wrapped a custom application with the Microsoft Intune Application Wrapper. So now that we have a custom application and an application enabled for management via Microsoft Intune that we are able to deploy them via Microsoft Intune and see the different behavior of the same application.
Looking at the screenshots below you see that with the custom application that “secure data” from the field can be copied within the application itself and to for instance an email.
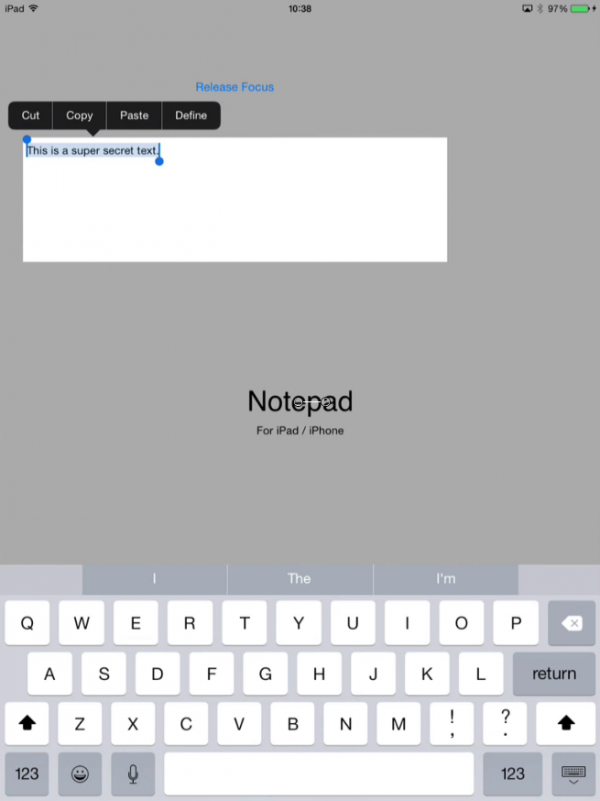
Step 1 copy the super secret text
Lets first copy some super secret text.
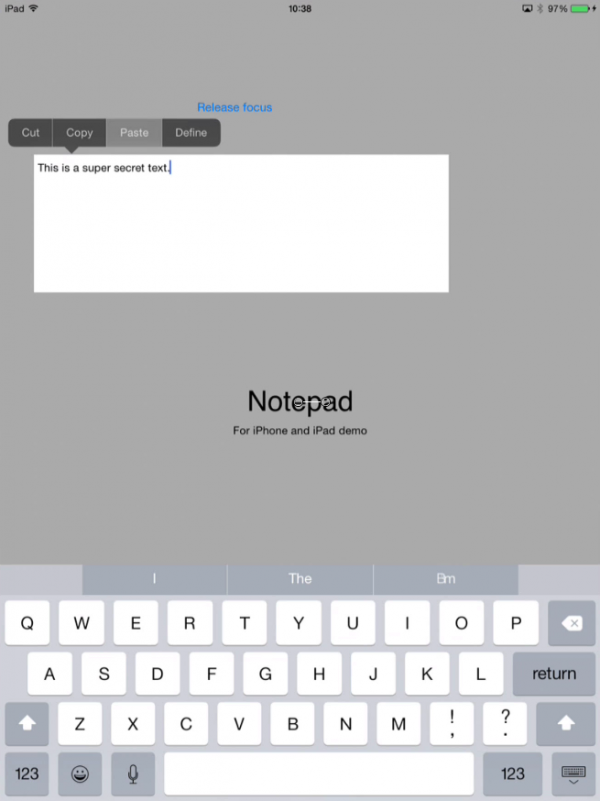
Step 2 paste the data within the application itself
Next step is to paste the super secret text into a second page of the application itself.
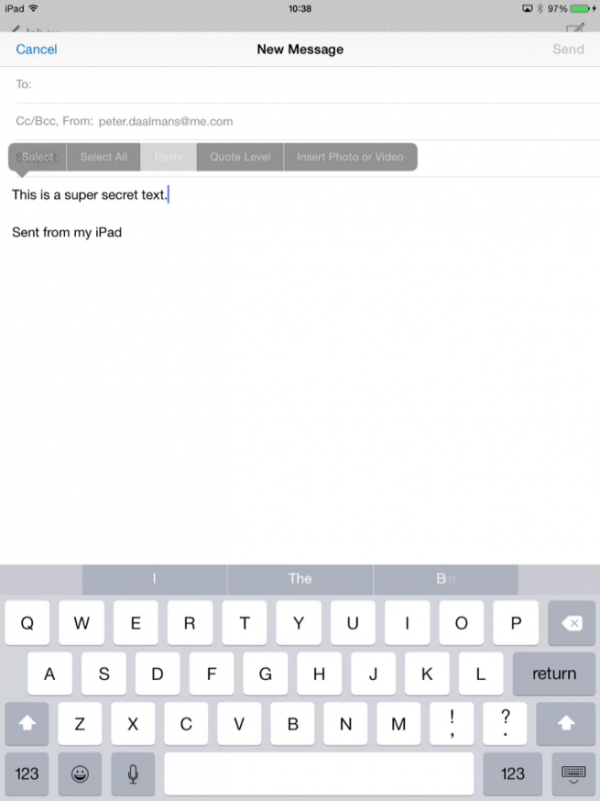
Step 3 paste the data in an email
Next step is to paste the super secret text into the native email application, as you see this is possible.
So next we want to secure the application like we did in the second blog post and make it available in Microsoft Intune. So the first step is to create a Mobile Application Management Policy for iOS.
For this post we only want to control that the secure data is not exchanged between the managed application and for instance the email app. In maybe one of my next blogs we will have al look at how the other settings can be used with this custom LOB 😉 app.
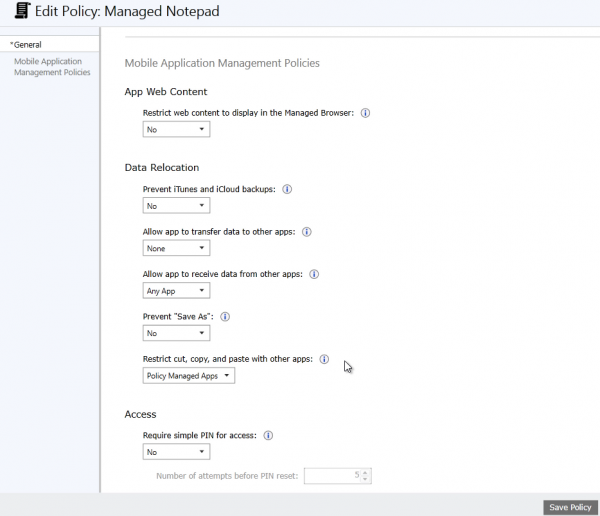
Currently the following settings can be managed.
| Serting | Description |
| Restrict web content to display in the Managed browser | Links in this application can only be launched in a managed browser, not in the native browser. Currently no Managed Browser is yet available for iOS. |
| Prevent iTunes and iCloud backups | The data of the app will not be allowed to be backuped to iTunes or iCloud |
| Allow app to transfer data to other apps | Specifies which applications can launch and send data to other apps using URL schemes |
| Allow app to receive data from other apps | Specifies if applications can launch and send data to this apps using URL schemes |
| Prevent “Save As” | Disables a “Save As” option in the app, if available. |
| Restrict cut, copy, and paste with other apps | This option are we going to use, we are able to control if we are able to cut, copy and past with apps and if so what kind of apps. (managed or not) |
| Require simple PIN for Access | To be able to use the app, a user neet to enter a PIN before the app can be started. The PIN is shared between apps from the same publisher. |
| Require corporate credentials for access | The user needs to supply the corporate credentials to be able to access the application. |
| Require device compliance with corporate policy | The application cannot be used when the device is not compliant with the corporate policy. |
| Recheck the access requirement after (minutes) | If a application is started or resumed the access requirements are rechecked if the timeout is expired. |
| Encrypt data | Specifies when data for this app is encrypted, to be able to encrypt the data a pin must be set. |
So now we have a MAM policy we need to upload the application that is wrapped by the Microsoft Intune App Wrapping Tool to Microsoft Intune.
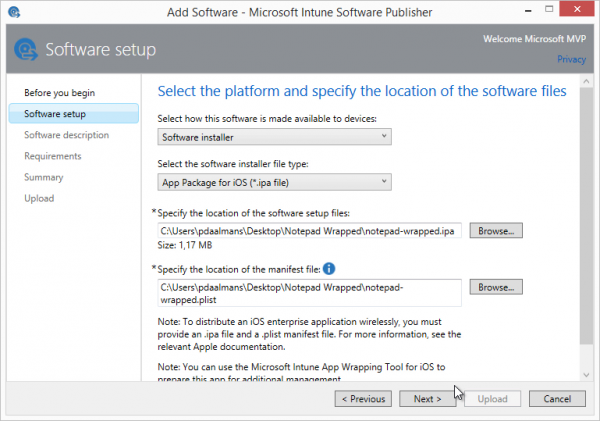
While deploying the Wrapped Notepad Application we need to choose the preconfigured Mobile Application Management policy, like shown below.
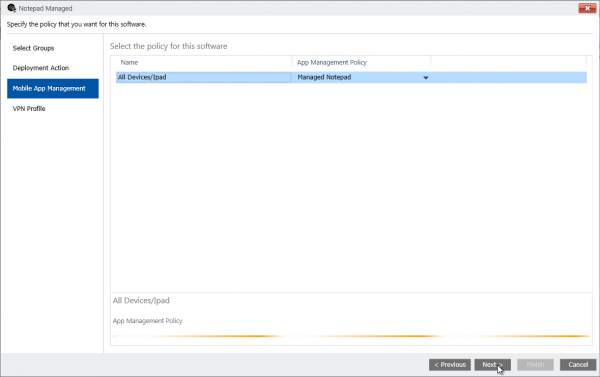
So after deploying and installing the Application on the iOS device we notice that the Application is now managed!

Step 1 copy the secure data
And again we copy the super secret text.
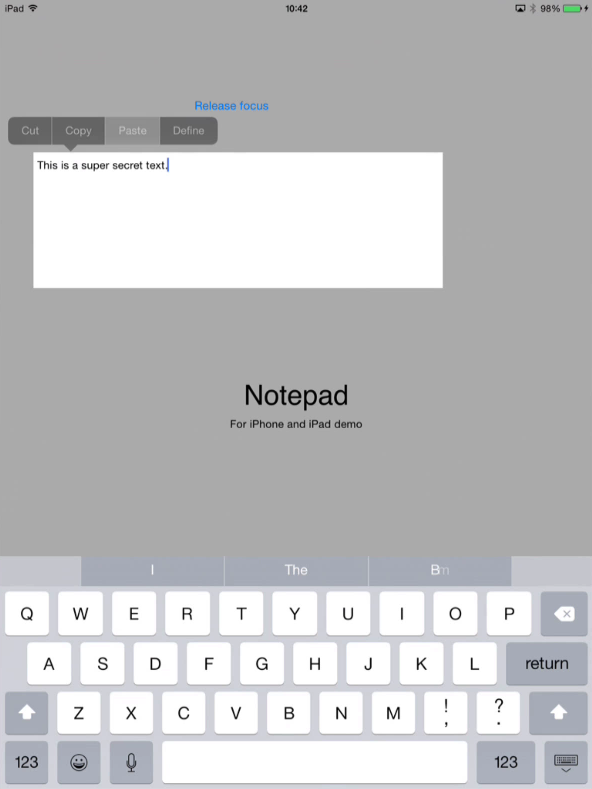
Step 2 paste the data within the application itself
Next step is to paste the super secret text into a second page of the application itself, which we are still allowed to do.
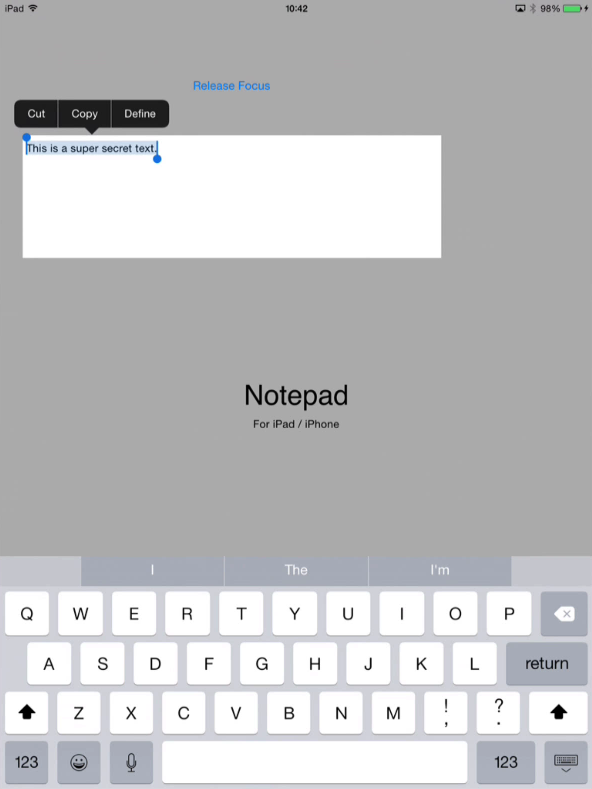
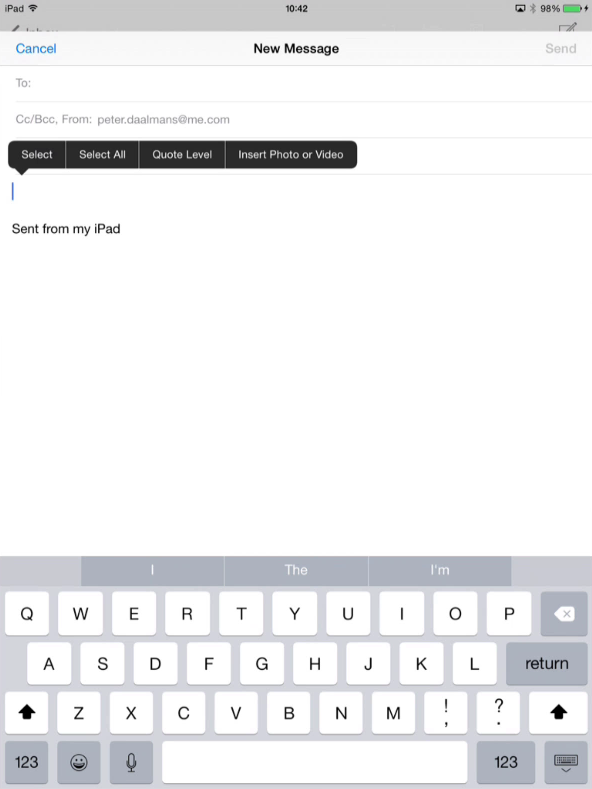
Step 3 paste the data in an email
Now we see that the paste option is not available and that the secret text cannot be copied into the native email application.
The MAM policies within Microsoft Intune are a really addition to the Microsoft Enterprise Mobility Suite. As soon as possible I will be adding a webcast showing this behavior in action so stay tuned!
Till next time!


