 In the series about the features of Configuration Manager 2012, earlier blogs mentioned, the new console, client settings, the application model and software center. Let’s talk today about another real nice and new feature within Configuration Manager 2012, Role Based Administration.
In the series about the features of Configuration Manager 2012, earlier blogs mentioned, the new console, client settings, the application model and software center. Let’s talk today about another real nice and new feature within Configuration Manager 2012, Role Based Administration.
In earlier versions of Configuration Manager it was always a big hassle to delegate rights to administrators within a Primary Site. You were able to add Primary Sites to your hierarchy for decentralized administrative purpose, for instance if a division of you company need to administer their own Configuration Manager objects. The Role Based Administration feature eliminates the earlier need of tiered Primary Sites for decentralized administration. The Role Based Administration data is global replicated data, this means that when you define your roles and role assignments at the Central Administration Site that they are valid at all child sites in the hierarchy.
The Role Based Administration feature is built of the following components:
Security Role
What types of objects can an administrator see and what is an administrator able to do with them?
Security Scope
Which instances can an administrator see and interact with?
Collection limiting
Which resources can an administrator interact with?
Out of the box Administrative roles
The Role Based Administration feature comes with 15 out of the box rules and it allows you to map organizational roles of administrators to security roles within Configuration Manager 2012.
Application Administrator
Grants permissions to perform both the Application Deployment Manager role and the Application Author role. Administrative users who are associated with this role can also manage queries, read and modify site permissions, and manage collections and the settings for user device affinity.
Application Author
Grants permissions to create, modify and retire applications. Administrative users who are associated with this role can also manage packages and programs, alerts for those applications and they can view status messages.
Application Deployment Manager
Grants permissions to deploy applications. Administrative users who are associated with this role can view a list of applications, and they can manage deployments for applications, alerts, templates and packages, and programs. Administrative users who are associated with this role can also view collections and their members, status messages, queries, and conditional delivery rule
Asset Manager
Grants permissions to manage the Asset Intelligence Synchronization Point, Asset Intelligence reporting classes, software inventory, hardware inventory, and metering settings.
Compliance Settings Manager
Grants permissions to define and monitor compliance by using the Desired Configuration Compliance feature. Administrative users who are associated with this role can create, modify, and delete configuration items and baselines. They can also deploy configuration baselines to collections, initiate compliance evaluation, and initiate remediation for noncompliant computers.
Full Administrator
Grants all permissions in Configuration Manager except reporting. The administrative user who first creates a new Configuration Manager installation is associated with this security role, the All scope, and all collections.
Infrastructure Administrator
Grants permissions to create, delete, and modify the Configuration Manager server infrastructure and to perform migration tasks.
Operating System Deployment Manager
Grants permissions to create operating system images and deploy them to computers. Administrative users who are associated with this role can manage operating system installation packages and images, task sequences, drivers, boot images, and state migration settings.
Operations Manager
Grants permissions for all actions in Configuration Manager except for the permissions that are required to manage security, which includes managing administrative users, security roles, collections, and security scopes.
Read-only Analyst
Grants permissions to read all objects in Configuration Manager.
Remote Tools Operator
Grants permissions to run and audit the remote administration tools that help users resolve computer issues. Administrative users who are associated with this role can use the Configuration Manager console to run the out of band management console, and to run remote control, Windows Remote Assistance, and Remote Desktop Services.
Security Administrator
Grants permissions to add and remove administrative users and to associate administrative users with security roles, collections, and security scopes.
Software Update Manager
Grants permissions to define and deploy software updates. Administrative users who are associated with this role can create collections, software update groups, deployments, templates, and enable software updates for Network Access Protection .
How does it work?
To see how things work lets handle a case described here below:
Case:
An application administrator (jjohnson) in the Netherlands needs to be able to administer all the Dutch applications and the application administrator needs to be able to deploy it to Dutch users and systems.
Solution:
First you will need to define a scope named “Dutch applications” and set the security scope for the Dutch applications. In this example I will use Acrobat Reader 8.1.2.
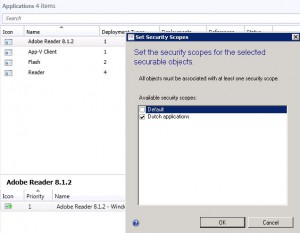
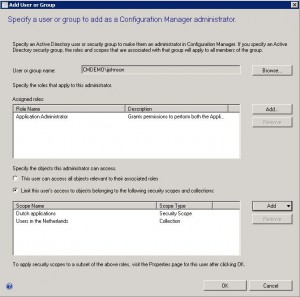
You need to assign the application administrator to the Application Administrator role, after that you need to assign the “Dutch applications” scope and “Users in the Netherlands” collection to limit the collection scope where the application can be deployed to.
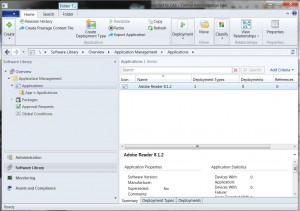
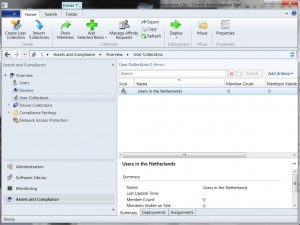
After the user jjohnson logs on, the user will only see the application Acrobat Reader 8.1.2 and the collection “Users in the Netherlands”
To read earlier blogs in this series see the following blogs:
- The features of Configuration Manager 2012 overview – part 1
- The features of Configuration Manager 2012 overview – part 2


